The newsmaking case of South Korean web hosting provider surrendering to ransomware deployers is one of a kind because the ransom paid amounts to $1 million.
It’s common knowledge that ransomware distributors are proficient in exploiting security vulnerabilities in the architecture of different computer systems. Whereas crypto attacks fired at Windows machines have become almost mundane, the Linux environment is relatively new ground thus far. Nayana, a web hosting provider based in South Korea, was unlucky enough to learn how devastating the latter type can get. Its IT infrastructure was compromised by a ransomware strain called Erebus as of June 10.
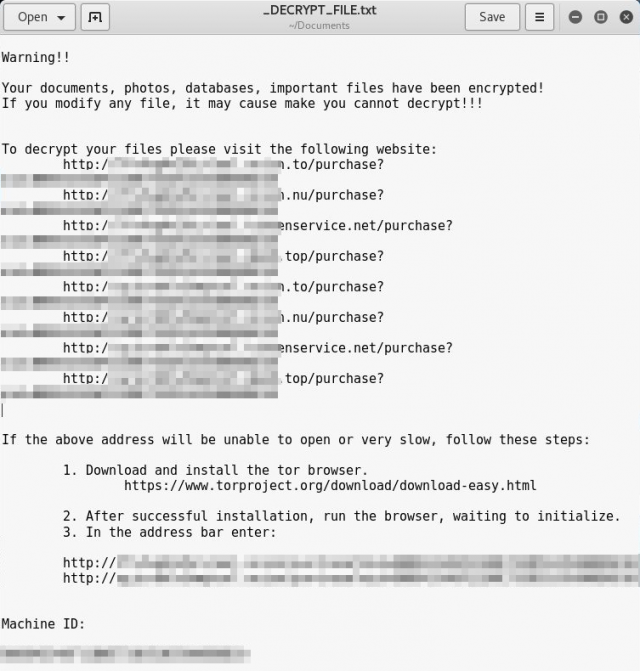
This infection isn’t new, but its previous editions zeroed in on Windows only. The latest variant of Erebus reportedly encrypted data stored on 153 Linux servers belonging to the web host. The predicament turned out to be double trouble as more than 3,400 customer websites were affected in the aftermath of the attack. The ransomware dropped ransom notes named _DECRYPT_FILE.txt (see below) and _DECRYPT_FILE.html, which instructed the users of hijacked machines to visit one of Tor based payment pages listed in the decryption how-to.
Ransom note dropped by Linux edition of the Erebus ransomware
Obviously, it was in Nayana’s best interest to sort things out and get its servers up and running as quickly as possible. The hurdle was that the attackers, who apparently realized how high-profile the target was, asked for 550 Bitcoin (about $1.4 million). As a result of days of negotiations with the crooks, the company officials were able to reduce the amount to 397.6 Bitcoin, which is roughly the equivalent of $1 million. The threat actors also agreed to obtain this amount in three installments. The infected organization submitted two of these tranches by June 17 and shortly announced the beginning of recovery process. The IT executives estimated it would take up to 10 days to decrypt information on all affected Linux servers.
Security analysts who looked into this defiant incident revealed that the web hosting provider’s website ran on out-of-date Linux kernel and used 11-year-old versions of Apache and PHP. While the actual breach vector in this particular case has not been verified by now, the above unpatched components certainly made Nayana a low-hanging fruit for perpetrators. In summary, there’s always a price to pay for gaping security holes, and it may reach millions.