A North Carolina school district fell victim to a combo or an extortion attack and a data breach executed by the SunCrypt ransomware gang.
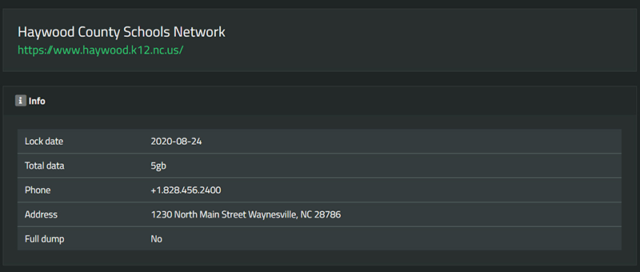
On August 24, 2020, the Haywood County Schools district in North Carolina reported a ransomware incident. The raid coerced the district’s officials to shut down its computer network and stop remote education projects. The impacted entities include the servers as well as all web-based and telephone services. A week later, the remote learning program was put back on track, but some services continue to be unavailable.
The onslaught entailed a data breach
According to internal investigation, the adversaries were able to steal data before launching the extortion attack. Security researchers also discovered that the incursion was perpetrated by the group in charge of the SunCrypt Ransomware.
This syndicate follows a recent trend of exfiltrating an infected organization’s files before triggering the encryption part of the attack. Then, the criminals contact the victim and state they will leak the information unless they receive the ransom.
After the school district refused to pay up, the malefactors carried through with their threats by uploading 5GB worth of data extracted from the contaminated network. The records include a slew of documents as well as personal details relating to students and teachers.
A quiet attack mechanism
Having gained an initial foothold in a network, SunCrypt ransomware actors generate a PowerShell (*.ps1) script whose name matches that of the organization. They store this script on the Windows domain controller repository. When fired up on a computer, it executes the ransomware and applies a cipher to make the stored files inaccessible.
In order to extend the reach of the attack, the crooks run a specially crafted batch file on every machine found on the same network. This routine will last until the data on all Internet-facing devices is encrypted. The felons covertly amass potentially important files before deploying the ransomware throughout the network in one hit. This way, they evade detection and manage to encrypt all machines quickly.
As soon as the unauthorized cryptographic job is completed, the victims discover that their files have been locked down and appended with random extensions. The malicious program also leaves a ransom note inside each folder, listing steps on how to access the Tor page that contains a chat feature for negotiating the recovery terms.
At this point, there are no known flaws in the cryptographic implementation of the SunCrypt ransomware. Therefore, the data cannot be restored without the secret key kept by the ransomware operators.