The distribution of Locky, one of last year’s most prolific families of crypto ransomware, has been on a downward curve since the beginning of 2017.
Having surfaced in February 2016, the Locky ransomware became a real online scourge for tens of thousands of home users and organizations. The spam waves delivering its malicious payload were extremely massive, making the Trojan one of the most widespread samples throughout the year.
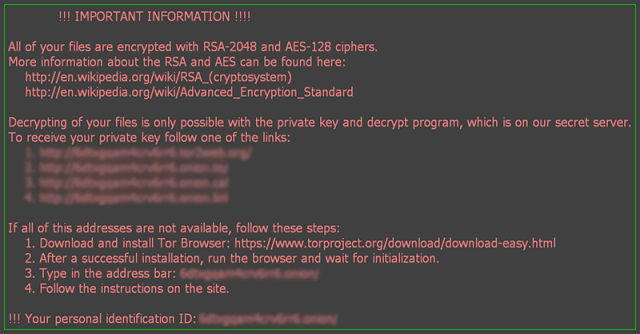
The infection features a robust cryptographic mechanism that does not allow for brute-forcing or otherwise cracking the private RSA decryption key. It spawned a total of least eight variants differing in behavioral properties, including the ransom notes and extension appended to affected filenames. A few of the latest ones were the .Thor, .Aesir, .Zzzzz, and .Osiris extension editions.
Ransom note dropped by Locky
The dominant position of Locky in the ransomware ecosystem started swaying in early January 2017. IT security researchers first associated this trend with fluctuations of the underlying Necurs botnet’s activity. Pre-Locky, this malware distribution network had been involved in deploying the banking Trojan called Dridex. Normally, botnet operators tend to take a holiday break for Christmas and New Year festivities, so analysts originally anticipated the ransomware propagation to revive.
However, according to Cisco’s Talos Intelligence Group, the volume of Necurs-powered spam spreading Locky never reached its earlier heights afterwards. No new variants have been released by the threat actors since December 5, 2016. Furthermore, stats by ID Ransomware, an online project aimed at helping ransomware victims identify different data-encrypting strains, also prove a dramatic drop in Locky samples uploaded last week.
Despite the fact that this plague seems to be struggling without the affiliated botnet’s assistance, its architects appear to be still keeping the propagation at a certain low level via alternative channels. So users should treat suspicious emails with caution, especially ones impersonating FedEx and UPS. Also, data backups are now more relevant than ever, so be sure to maintain them and thus mitigate the damage of a possible ransomware compromise.